16 Well-Paying Positions in Prepackaged Computer Software
There are numerous high-paying positions and numerous career options in the prepackaged computer software sector. Additionally, those who enjoy utilizing computers and have strong problem-solving abilities might consider careers in this field. Deciding if this is the correct career option for you might be made easier by learning more about the sector.
This article examines sixteen well-paying positions in the computer prepackaged software industry.
What is bundled software for computers?
Software that is created, packaged, and offered for sale to customers or companies in an executable format is known as computer prepackaged software. It is commercial software that offers particular features and functionalities, like accounting, graphic design, word processing, spreadsheets, and video editing. This is in contrast to custom software, which is created to specifically address the requirements of a given user or company.
Prepackaged software is meant to be used by a larger range of users and is frequently made to be simple to install and operate. Along with training materials, updates, and patches to address bugs and provide new features, it could also include customer support.
16 positions in bundled computer software
Here are sixteen well-paying positions in computer software that come in packages:
1.The solution architect’s main responsibilities:
An expert in the field, a solution architect is in charge of creating comprehensive technological solutions that satisfy user demands and organizational objectives. They assess and evaluate user needs and create software solutions that address them in collaboration with clients, software development teams, and others. They choose software tools and components, supervise the production of system architectures, and guarantee the scalability and maintainability of the software. Additionally, as regular development develops, they can be asked to examine and approve software code.
2.A tester for quality assurance
The main responsibilities of a quality assurance tester are to guarantee the dependability and quality of software programs. In cooperation with software development teams, they could test and validate the usability, performance, security, and functionality of software. Creating test cases, running them, and then locating and recording any software flaws that surface during this process could all be part of the job description. After that, it might be necessary for them to give software development teams input regarding what they discovered.
3.A technical assistance professional
The main responsibilities of a technical support expert are to help clients or end users who are having problems with software, hardware, or other specialized items by offering technical support and assistance. They offer phone, email, or in-person support to users in addition to diagnosing and troubleshooting technological difficulties. Furthermore, they are able to troubleshoot complicated issues with their specialized knowledge and provide clients or end users with training to advance their technical knowledge and skills.
4.An engineer for clouds
The key responsibilities of a cloud engineer include developing, constructing, and maintaining cloud computing services and infrastructure. Furthermore, they collaborate with many cloud-based platforms to provide solutions that support enterprises and organizations in leveraging this technology. They are responsible for developing cloud architecture, setting up virtual machines and networks, monitoring performance, diagnosing problems, and guaranteeing security and compliance. To guarantee that services and apps are seamlessly integrated with cloud infrastructure, they can also collaborate with development teams.
5.A programmer
A software engineer’s main responsibilities include designing, creating, and testing software platforms, systems, and applications. They are able to create software solutions that satisfy users’ expectations by analyzing their requirements. Software engineers have expertise creating safe and functional software using a variety of coding languages. To guarantee smooth software development and deployment, they may have to work in tandem with other teams, including those in charge of quality assurance and product development.
6.Full-time programmer
Main responsibilities: Updating web applications’ front-end and back-end software is the responsibility of a full-stack developer. It is reasonable to anticipate that they will work with and be skilled in a variety of programming languages, including HTML, CSS, JavaScript, Python, Ruby, and SQL. Developing and designing server-side components, integrating third-party services and APIs, testing and debugging apps, and managing code repositories are a few of the tasks they could be assigned. In order to guarantee high-quality software development, this role may also require cooperation with other developers and teams.
7.Engineer for systems
A system engineer’s key responsibilities include designing, implementing, and maintaining intricate computer networks and systems. They collaborate with software and hardware components to guarantee dependability, security, and performance. They are responsible for evaluating user requirements, creating system architectures, installing and setting up hardware and software, keeping an eye on system performance, and creating upgrades and additions for the system. In order to guarantee system effectiveness and functionality, they also work together with other IT teams and stakeholders.
8.Scientists with data
The main tasks of a data scientist are to analyze large, complicated data sets in order to find trends, patterns, and insights that help guide business choices. They make use of Python, R, and SQL, as well as statistical modeling tools. Furthermore, they can employ data cleaning and processing methods, statistical analysis, and modeling, along with data visualization tools that help stakeholders understand data and facilitate the creation of data-driven solutions, by utilizing their training and qualifications in these areas.
9.A network analyst
The major responsibilities of a network analyst are to design, build, and maintain computer networks for companies and organizations. Utilizing their expertise in managing hardware and software components of networks, they guarantee network dependability, security, and efficiency. They are responsible for assessing the needs for the network, creating network architectures, and, if necessary, setting up and installing hardware and software. In order to guarantee network efficiency and operation, they could also work together with other IT teams and stakeholders.
10.A tester of software
Software testers’ main responsibilities include making sure software applications are dependable and of high quality before making them available to end users. They collaborate with software development teams to test many facets of computer programs and apply their knowledge to find and report bugs in the software. Among their responsibilities are writing test reports, carrying out extensive testing, working with developers to address software flaws, and taking part in code reviews. To improve testing accuracy and efficiency, a software tester can make use of automated testing tools and frameworks.
11.The architect of software
Developing and designing the architecture of software systems, platforms, and applications is the principal responsibility of a software architect. Users study and determine user requirements, then work with software development teams, project managers, and stakeholders to create software solutions that provide the functionality users need. As a crucial component of their work, they create system designs, using their skills to choose and apply the right systems to produce the finest software.
12.Engineering manager for development and operations
- Principal tasks:
Software application development, testing, and deployment must go smoothly and efficiently, and this is the responsibility of a development operations (DevOps) engineer. To establish and oversee automated software deployment procedures, maintain code repositories, and guarantee software configuration management, they draw on their experience working with developers, testers, and other IT specialists. Their responsibilities also encompass creating and overseeing application security and performance, debugging problems, and collaborating with interdisciplinary teams to guarantee the smooth delivery and development of software.
13A professional in IT security
Among their main responsibilities is the security and integrity of computer systems, networks, and data inside an organization. They employ their expertise in IT and security tools to recognize, evaluate, and create security procedures that will put security countermeasures in place for risks and vulnerabilities. Managing security hardware and software, keeping an eye on security logs, enforcing security policies and procedures, creating incident response plans, and educating end users on security are some of their other responsibilities.
14.A programmer for computers
Writing, testing, and maintaining computer software programs are the key responsibilities of a computer programmer. They can create and implement software solutions that satisfy user requirements using a variety of programming languages, including Python, C++, Java, and others. Writing and testing code, troubleshooting software bugs, and recording software procedures and code are the main responsibilities of this profession. Additionally, they can use the tactics and approaches they have learned to solve obstacles that come with programming by drawing on their expertise.
15.Developer for mobile apps
The main responsibilities of a mobile developer are to design and develop mobile applications for different platforms using their knowledge and expertise. They might utilize Swift, Kotlin, or Java as programming languages, and they might work with mobile development frameworks. In addition to creating and testing code, they also design and test user interfaces, troubleshoot software bugs, integrate mobile apps with backend systems, and guarantee the dependability, security, and performance of mobile applications.
16.Developer of websites
A web developer’s key responsibilities include designing, creating, and maintaining websites and web apps. They might use web technologies like HTML, CSS, and JavaScript in addition to working with web development frameworks like React, Angular, or Vue. Their responsibilities may involve taking different actions to guarantee the web application they are constructing operates effectively, securely, and dependably. They might work in a team environment and regularly give the customers they serve updates and criticism.
Conclusion
We have provided as much information as we could regarding careers and jobs in computer software and prepackaged software. Now that you’re persuaded, you realize how important it is to forge a successful career in computer software and the packaged software sector. Being proficient in your field (web development, software engineering, etc.) can enable you to hold better positions and command more pay in any company. Jobs in this sector pay well and offer a highly pleasant work environment for employees.
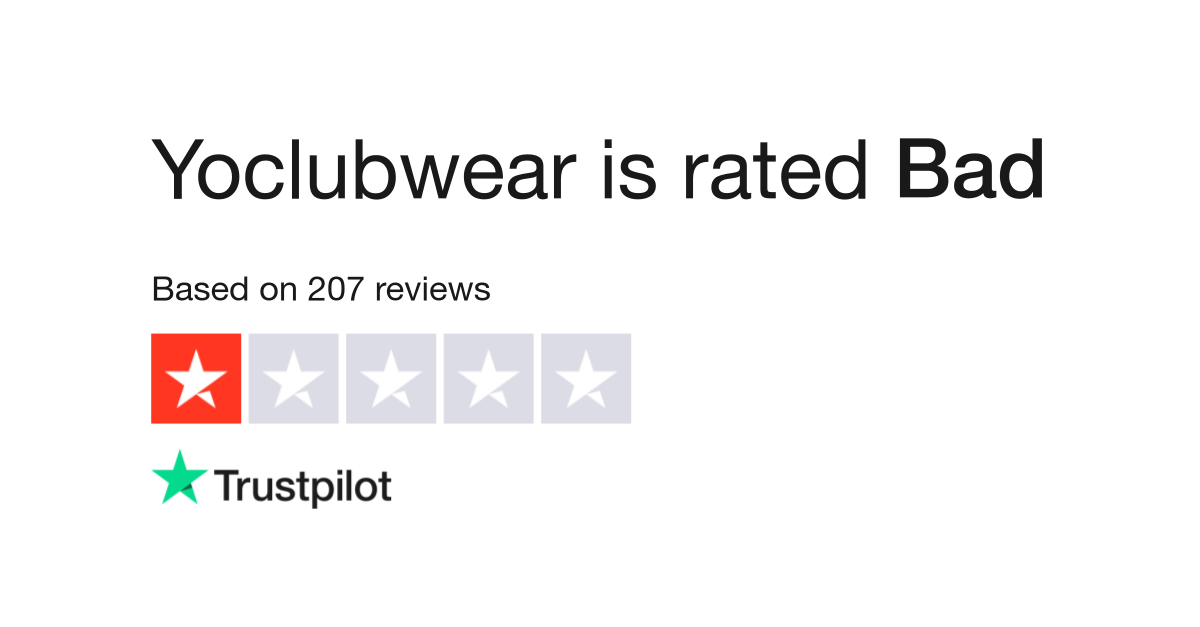
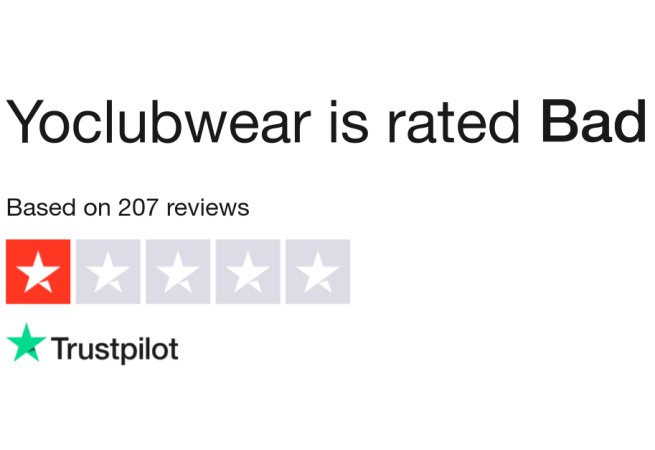
Yoclubwear Scam Store | Things you should know
Introduction
You should stay away from Yoclubwear.com at all costs, as it is a phony internet retailer. This fraudulent website offers a wide range of products at extremely low costs, but in reality, you will either receive subpar or counterfeit goods or nothing at all.
This post will explain the workings of the Yoclubwear.com scam, point out warning signs to look out for, and—most importantly—offer advice on how to guard yourself against falling for this and similar scam websites.
Scam Overview
At first glance, Yoclubwear.com seems to be a reputable online store offering a range of reduced products to customers at costs far lower than those of big-box stores. In actuality, though, Yoclubwear.com is a fraudulent website that uses deceptive methods to fool users into placing orders and providing sensitive personal information or money.
Yoclubwear.com scammers use social media sites like Facebook, Instagram, and TikTok, as well as spam emails, to advertise their website and trick unsuspecting people. This scammer website tricks naive customers with absurdly low prices and pilfered product photos.
Scammers just grab the money and disappear after victims place orders and provide payment details. Clients are left with any of the following results:
- The most typical result is nothing at all. After funds are completed, orders remain unfilled and merely vanish.
- Cheap imitations or subpar replacements — The items that victims get can be knockoffs or low-quality copies that don’t match the original product specifications.
- Goods that are obviously worn, broken, or otherwise tampered with – In certain instances, victims report receiving goods that indicate no new things are being supplied.
- Erroneous products: A few orders show no order accuracy at all because the things come entirely different from what was ordered.
In addition to selling fake goods or none at all, Yoclubwear.com dishonestly gathers personal and financial information from clients at the point of sale, including complete names, home addresses, phone numbers, credit card information, and more. It’s likely that this data is sold or utilized for illegal activities, including credit card fraud, identity theft, and sharing on dark web markets.
According to our investigation, Yoclubwear.com is probably a component of a bigger, Chinese-based fraud network that is connected to one another. This network runs a plethora of fictitious e-commerce websites with the primary goal of misleading consumers.
There are warning signs that this company is not authentic. Legislative papers are plagiarized and devoid of authentic policies. Customer service cannot be contacted in any way. The proprietors of this website have not been identified. Shoppers are intended to be lured in by unrealistic discounts of up to 90% off. Major merchants are the source of all product information theft. No social media presence is present.
How does the fraud at Yoclubwear.com operate?
To trick shoppers into purchasing fake or nonexistent goods, Yoclubwear.com employs a number of dishonest strategies. The con operates as follows:
Promoted by social media advertisements and spam emails
The con artists relentlessly advertise Yoclubwear.com via avenues such as:
- Emails that are spam and provide links to the fake website.
- Fake ads displaying enormous product discounts can be found on Facebook, Instagram, and TikTok.
- Fake reviews or news reports lauding Yoclubwear.com sales.
- These strategies are meant to trick search engines and lure unsuspecting users to the website.
Strategies of Bait and Switch
Following the placement of orders and payment, clients receive:
- Just pilfered money—nothing at all.
- Cheaper knockoffs as opposed to promoted goods.
- Replace new items with repurposed or altered ones.
Ignores grievances from customers
Shoppers who have been deceived and wish to report or request a refund from Yoclubwear.com are:
- Disregarded in full.
- Encountered with e-mail or account blocking.
The phony website Yoclubwear.com entices consumers with false marketing, collects money but never delivers the goods, and bans users who file complaints. These dubious tactics dodge providing responsible customer service and enable the scam to go on.
Warning Signs at Yoclubwear.com
Yoclubwear.com has a lot of warning indicators that point to it being a scam website posing as an established online business. Astute shoppers need to be aware of the following warning signs:
Scam Network Segment
According to research, this website is a component of a larger, Chinese-based, network of scammers. The only goal of this network is to deceive clients by running a variety of phony retail websites.
Duplicated court documents
This website appears to have plagiarized its Terms of Service, Privacy Policy, About Us, and other legal pages from well-known scam websites. Plagiarism on official pages is a common tactic used by scammers to give their websites the appearance of legitimacy. The policies, however, probably don’t apply to this website or provide any real user protection.
Details of Contact
This website does not offer live chat, a phone number, or a physical address for customer service. Customers can’t contact the company with problems because it doesn’t have its contact information.
Unnamed Business
Regarding who owns or runs the company, this website is utterly opaque. Don’t trust opaque websites with your money or personal information.
Incredibly Low Discounts
Shoppers are enticed by extreme savings. However, legitimate businesses cannot continue to provide such exorbitant discounts that would indicate fake items.
Taken From Original Content
Images and product details are all plagiarized from other large retailers. Yoclubwear.com has no unique content, which exposes its falsity.
Not on any social media platforms
Reputable companies keep social media accounts to interact with their followers. It is quite strange and suspicious because Yoclubwear.com has no accounts at all.
We can conclude that Yoclubwear.com is a fraudulent website that online customers should steer clear of based on the aforementioned warning signs. There is no proof that Yoclubwear.com is a reputable company that offers its clients high-quality goods or services.
As a result, we suggest that you avoid making purchases from Yoclubwear.com or any other websites that exhibit the same warning signs. You’ll only run the risk of losing your money and private information to con artists who don’t give a damn about your well-being or security.
How to Recognize and Stay Away from Scammed Online Retailers Yoclubwear.com and other
Scam websites can be easily recognized despite their convincing appearance, thanks to a few warning signs:
Look Up the Company Information and a Valid Domain Name
Often, fake websites use well-known brand names or have strangely spelled domain names with extra words. Verify the legitimacy of the company by conducting an internet search for its name.
Verify the availability of a working phone number and email for customer care, as well as a real business address. The absence of valid contact information suggests a dubious supplier.
Search for Deals That Seem Too Good to Be True
Scam websites entice users by offering deals that are far cheaper than retail rates or spectacular reductions of 50–90% off. Real companies are not able to bear such high losses. A deal is probably too good to be true if it appears so.
Check the Company’s Credibility
- Look up any bad comments or scam reports online using the website, company name, and owner names. To find out about their reputation, check with the BBB, TrustPilot, and complaint forums.
- Review sites with no genuine consumer activity and no social media presence indicate that the reviews are probably from scammers.
Examine payment and site security options.
- Make sure websites have assured return procedures and SSL encryption. Payments and sensitive data shouldn’t be handled by unsecure websites.
- Only irreversible payments, such as wire transfers, gift cards, and bitcoin, are typically accepted by scam websites; credit cards with better fraud safeguards are typically avoided.
Identify grammatical mistakes, laws that prohibit plagiarism, and restricted merchandise.
- Fake websites don’t put the same kind of work into original legal policy writing and correct grammar as well-established firms do.
- A very small product selection that stays away from popular product categories is another sign of pop-up scams.
Shoppers can identify fraudulent retail outlets that aim to take advantage of their genuine client bases based on trust and accountability by carefully observing these warning indicators.
Frequently Asked Questions
How can one tell if Yoclubwear.com is a scam?
Stranger-than-fiction prices, cloned product descriptions, and missing contact details are warning signs.
Is Yoclubwear.com a secure place to shop?
Nope. Yoclubwear.com is a dubious website that has a lot of scammy traits. They probably sell either nothing at all or fake goods.
What do I need to do if my order from Yoclubwear.com has been placed?
Get new cards issued and report fraudulent transactions by getting in touch with your bank and credit card provider. Pay particular attention to accounts to ensure that financial data that has been taken is not being misused.
Conclusion
We recommend that you avoid visiting this dishonest website. Avoid being seduced by the alluring discounts offered. The customer service is nonexistent, and the product photographs are not real. By avoiding Yoclubwear.com and other similar websites, you can protect yourself.

Understanding the “Instagram User” Tag: A Comprehensive Guide
In the dynamic world of Instagram, encountering the “Instagram User” tag can leave many puzzled. This article demystifies the meaning behind this mysterious tag, drawing insights from the latest experience. Understanding this tag’s implications is vital to navigating Instagram’s social landscape, whether you encounter it in DMs or comments.
What it means to be an “Instagram User”
A user’s Instagram name is replaced with “Instagram User” when his or her account has changed status. This change can be attributed to several actions:
Deactivation or Deletion of Account: The user might have temporarily deactivated or forever removed their account, bringing about their profile being unavailable and their username being “Instagram User.”
Instagram has Banned: When an account works against Instagram’s rules, Instagram might banned it, bringing about the evacuation of the client’s profile and its supplanting with the “Instagram Client” tag.
Blocking: Assuming a record blocks you, you could likewise see this tag, which implies you never again approach view their profile.
Uncovering the “Instagram User” Secret
In order to understand what the “Instagram User” label implies in your situation, think about these differentiations:
Deactivated versus Deleted Records: Deletion is not reversible, completely removing all data from Instagram account. Deactivation is temporary, permitting user to enjoy some time off and get back with their followers and data flawlessly.
Banned Records: Instagram forces bans for any terms violation, making the account’s record substance and profile vanish, thus the “Instagram Client” tag.
Blocking: In contrast to deactivation or deletion, assuming you’re blocked, the profile actually exists yet blocks your admittance to the client’s profile and content.
Finding What Actually Has Occurred
This is the way you can deduce the exact reason for experiencing “Instagram User” display:
Look at Past Conversations: In the event that you can in any case see past DMs yet the account name has changed to “Instagram User,” it probably shows deactivation. In the event that you can’t send messages or view the profile, the User might be erased or you has been blocked.
Endeavor to Look: If looking for the account yields no outcomes or shows “User not found,” it proposes deactivation or deletion. On the off chance that others can see the account however you can’t, you’re probably blocked.
Look at Profile Openness: A clear profile or the failure to see any account subtleties further backings the instances of blocking or deactivation.
Exploring Instagram Connections
Grasping the subtleties of Instagram’s “Instagram User” tag can assist with dealing with your Social Media interactions all the more actually. Here are a few hints:
Openness is Of the utmost importance: If feasible, connect through other means to explain what is going on.
Regard the Protection and Privacy: Whether somebody has decided to have some time off from Instagram or chose to block you for individual reasons, it is central to regard their security and decisions.
Stay Updated: Get to know Instagram’s rules to keep away from inadvertent violations that could prompt record boycotts.
Ending Notes
The “Instagram User” label fills in as a sign for different changes to an Instagram account, including deactivation, deletion, or a ban by Instagram, or a block by the User. By understanding the explanations for this tag and how to find them, Instagram users can explore their social media cooperations with more noteworthy clarity and regard for others’ decisions. Keep in mind, while social media bonds us, regarding limits and protection stays vital in this computerized age.
FAQs:
Q: Might I at any point message a record labeled as “Instagram User”?
A: You can attempt, yet messages will not be conveyed in the event that the account is deactivated or blocked. In the event that you’re blocked, you will not have the option to send messages by any stretch of the imagination.
Q: How long does the “Instagram User” tag remain?
A: For deactivated accounts, the label stays until the account is reactivated. For deletion or prohibited accounts, it’s super durable except if the user makes another account.
Q: Is there a method for separating between a banned and a deactivated account according to the user’s viewpoint?
A: Without direct data from Instagram or the account’s owner, recognizing a ban and deactivation can be difficult for outside users.
By remembering these experiences, you can all the more likely comprehend and adjust to the developing elements of Instagram communications, guaranteeing a more educated and conscious commitment on the stage.

The Number of People Who Can Solve a Rubik’s Cube
Introduction
Within the world of brainteasers and puzzles, the Rubik’s Cube is widely recognized as a representation of perseverance and achievement. For decades, people have been fascinated and perplexed by this vibrant 3D puzzle.The number of people who can actually solve a Rubik’cubebe is a commonly asked question. Investigating the information, tactics, and elements that contribute to this fascinating phenomenon, let’s dive into the cube fanatic community.
The legendary 3D combination puzzle known as the Rubik’s Cube was created in 1974 by Hungarian architect and professor Ernő Rubik and is a challenge even for the sharpest minds. It looks very easy, but the intricate procedures and techniques needed to solve it are quite sophisticated.
Practically everyone has attempted to solve a Rubik’s cube. Usually, the first try ends in failure with nothing more than a disorganized tangle of colored cubies (what I will refer to as one little cube inside the larger Rubik’s cube) arranged in an illogical manner. After mastering a specific core set of methods known as macros, solving the cube becomes nearly effortless. The rationale behind these solutions’ moderate difficulty can be understood by applying fundamental group theory.
The Universal Appeal of the Rubik’s Cube
Appealing to the Inquisitive Minds
There is something about the Rubik’s cube that draws in a wide variety of individuals. People all throughout the world, young and old, are drawn to the challenge of cracking this surprisingly complex riddle. Because of its enduring appeal, puzzle-solving fans of all ages have something in common.
The Art of Problem Solving: From Novice to Expert
The Curve of Learning
To solve a Rubik’s cube successfully, one must grasp a number of algorithms and techniques. When they first start out, beginners frequently start with the layer-by-layer method and work their way up to more complex strategies. The number of people who can solve the puzzle proficiently is greatly impacted by this learning curve.
The Growth of Quick-Cubing
“Speedcubing” is the name of a subculture that has emerged alongside standard cube solving. People who are committed to solving the cube quickly, known as speedcubers, frequently use intricate techniques and quick finger movements. A committed global community of cubers has been drawn in by this competitive aspect.
Factors Influencing Solving Proficiency
Mental Capabilities and Visual Awareness
Solving the Rubik’s Cube requires a variety of cognitive skills, such as spatial awareness and logical reasoning. People who are naturally inclined to these abilities usually solve puzzles more adeptly.
Commitment and Exercise
The saying “skill comes with practice” also holds true for cubing. The likelihood of becoming proficient at solving the cube increases for those who invest the time and effort to learn and practice various problem-solving techniques.
Knowledge of Algorithms
Competent cubers are familiar with the algorithms required to work with the cube’s many layers. Completing puzzles successfully requires memorization and the use of these strategies.
Revealing the Figures: How Many Can Solve?
Worldwide Cubing Community
The online cubing community has grown more integrated as social media and other online platforms have gained traction. Hundreds of thousands of people have reportedly learned how to solve the Rubik’s cube all across the world, demonstrating a range of skill levels.
Competitions for Speedcubing
Competitors from all around the world enter speedcubing events. The remarkable quickness and skill of those who can solve the cube in a matter of seconds are demonstrated by these competitions. The rising interest in these contests is indicative of cubing’s expanding appeal.
Number of rectangles on a Rubik’s cube
Other cubes exist outside the conventional 3×3×3 Rubik’s cube, in which each side is divided into n pieces (n = 3 for the classic Rubik’s cube). A Rubik’s cube’s little squares on each surface can be joined to create larger rectangular shapes, regardless of color. The total number of possible rectangles (including squares) that can be created in this manner for an n×n×n Rubik’s cube should be calculated. 54 is the correct solution for the 2×2×2 cube.
Number of Squares on a Rubik’s cube
With 54 squares overall, the 3x3x3 cube is the most popular variety of Rubik’s cube. Among fans of Rubik’s Cubes, this cube is the most often utilized size and the standard size used in official contests.
Still, there are a number of other Rubik’s Cube varieties that differ in the quantity of squares they include. For instance, there are 96 squares in the 4x4x4 cube, compared to just 24 in the 2x2x2 cube. There are three other widely used variations: the 5x5x5 cube, which has 150 squares; the 6x6x6 cube, which has 216 squares; and the 7x7x7 cube, which has 294 squares.
Average Time to Solve a Rubik’s Cube
The average time needed for a cuber to solve a Rubik’s cube over several tries is referred to as the “average time.” The goal of a speedcuber is to finish the cube in the least amount of time possible. To account for variances in performance, the average time is determined by calculating the results of numerous solves.
There are various factors that can significantly affect how long it takes to solve a Rubik’s cube on average. The cuber’s skill level is one of the primary variables. Speedcubers with experience may solve the cube in seconds, while beginners may need many minutes or even hours. Because there are differences in the efficiency and speed of different solving techniques, these factors also have a major impact on the average time. Larger cubes typically take longer to solve than smaller ones, according to another factor that influences average time: cube size.
Average time is a common concept in speedcubing events, where competitors usually complete several solutions; their ranking is derived from the average of these solves. This helps to explain performance variances brought on by weariness, anxiety, or errors in certain situations.
With improvements in practice methods, solving strategies, and training, the average time to solve a Rubik’s cube has dropped dramatically in recent years, making the times among the best speedcubers extremely competitive. Let’s examine how typical solving times have changed historically in the next section.
Average time is a common concept in speedcubing events, where competitors usually complete several solutions; their ranking is derived from the average of these solves. This helps to explain performance variances brought on by weariness, anxiety, or errors in certain situations.
With improvements in practice methods, solving strategies, and training, the average time to solve a Rubik’s cube has dropped dramatically in recent years, making the times among the best speedcubers extremely competitive. Let’s examine how typical solving times have changed historically in the next section.
Conclusion
The Rubik’s Cube comes in various varieties. In theoretical research and application, some progress has been made. This study thoroughly reviewed the history and evolution of the Rubik’s Cube, dissected its structure and functionality, and assessed its current state of research, covering its applications in science, restoration algorithms, and other domains.

Mastering Attitude in Your WhatsApp About Lines: A Guide to Making a Statement
In this digital age, just like our real-life, our online personas have also become equally important. So the WhatsApp About lines are one of the online places where our personality shines. That’s exactly the place where you can show your beliefs, attitude and unique flair. Crafting the perfect WhatsApp is an art either you are looking for, inspiring your
friends or making a statement. In this article, we will have a look on how to use this small but powerful space effectively to reflect your personality and attitude.
Understanding the Importance of Your WhatsApp About Line
The WhatsApp line is not only a few words under your name but also a reflection of your attitude and personality. When people open your profile it’s the first thing that is seen so making it charming should be your priority. A well-established, well-managed and well-written About line can leave an everlasting impression on your friends, family and colleagues or whoever viewing your profile.
Crafting the Perfect Attitude in Your About Line
Keep it short and sweet: You should keep balance between length and impact because the best WhatsApp About lines are short yet powerful. Every word matters, so make every word count.
Reflect your personality: Whatever you are a poet, an engineer, model or philosopher, your About line should reflect your personality and profession. Authenticity with a blend of attitude is more important than artificial non-matching words.
Be Creative: You should stand out from the crowd with something eye-catching by using some unique words or quotes that actually reflect your inner attitude.
Update Regularly: As per your current situation, your About line should be updated regularly. One shouldn’t be afraid of doing this.
Aggressive and attitude Lines:
Here are some WhatsApp about lines, that depict your attitude and power face:
“My life. My rules. My attitude. My mistakes. Who the hell are you to judge me?” – A statement that shows independence and defiance.
“I show attitude because I think my hard work has made me deserve it.” – This line reflects a sense of earned attitude and self-respect.
“Be Silent And Let Your Success Shout.” – A proud yet somewhat aggressive line indicating that success speaks louder than words.
“Haters gonna hate, but I’m gonna keep shining.” – This line conveys a defiant attitude towards critics.
“I don’t chase people, I chase dreams.” – Reflects a focused and somewhat aggressive attitude toward personal goals but ignoring distractions.
“People in Shocks I’m in Rocks.” – Suggests a proud and unbothered behavior for others’ reactions.
“There are three sides to an argument.. my side, your side, and the right side.” – Shows a confident and easy approach to disagreements.
“If you can’t handle my attitude then stop being around me.” – This line is bot aggressive and proud, reflects don’t jump into my circle if you do not have relevant skills to understand me.
“I am too preoccupied with tending to my own responsibilities to compare them with yours.” – Indicates a focus on self and a disregard for others’ opinions or comparisons.
“Your opinion doesn’t define me.” – A proud and attitude-oriented statement of self-confident and independence from others’ opinions.
More advance:
Here’s a diverse collection of WhatsApp about lines with an attitude theme, drawn from various sources:
Humorous lines like “I never argue, I just explain why I’m right” and “My therapist says I have a preoccupation with vengeance. We’ll see about that”.
For those feeling solitary, options include “Solitude is my closest companion, the one who understands” and “Alone but not lonely, for my thoughts are my best friends”.
Poetic and aesthetic choices like “Whispering poetry to the moon, one star at a time” and “In the silence of simplicity, I find profound beauty”.
Cool and stylish options such as “In the kingdom of cool, I reign” and “Born in the cool, raised in style”.
Nature lovers might prefer lines like “In nature, I find my peace” and “Nature is my therapy”.
Funny lines for a lighter touch, including “I’m not clumsy; I’m just on a mission to test the durability of objects” and “My superpower is making the most awkward situations even more awkward”.
Attitude-focused options such as “Maybe you should hustle as hard as you overthink” and “I am a Butterfly in the form of a Girl. Pretty to Admire, but Difficult to catch”.
Inspirational quotes including “It’s your road and yours alone; others may walk it with you, but no one can walk it for you” – Rumi and “Your time is limited, so don’t waste it living someone else’s life” – Steve Jobs.
Strong attitude statements like “My life. My rules. My attitude. My mistakes. Who the hell are you to judge me?” and “Be polite in your words and savage in your attitude”.
For a minimalist approach, one-word options include “Loving”, “Fierce”, and “Girlboss”.
Self-affirming lines such as “My vibe attracts my tribe” and “I’m not weird; I’m a limited edition”.
Love-focused quotes like “Nothing is best, but when I am with you everything is best” and “True love never ends”.
Motivational lines including “Action is the foundational key to all success” and “The doors will be open to those who are bold enough to knock”.
For a strong personal stance, lines like “Haters gonna hate, but I’m gonna keep shining” and “I don’t have time for negative vibes” are suitable.
Meaningful lines such as “Being soft is being brave” and “Silence is a powerful scream”.
Singles might like “A king is more powerful without a queen. Enjoy being single!” and “Being single means riding solo and enjoying life”.
New blend of Attitude-Driven WhatsApp About Lines
For the Optimist: “Living in a sunshine state of mind.”
For the Humorist: “Currently starring in my own reality show titled, ‘A Modern Cinderella; One Girl’s Search for Love and Shoes.'”
For the Philosopher: “In the pursuit of not just existing, but truly living.” For the Mysterious: “A riddle wrapped in an enigma.”
For the Motivated: “Dreaming with my eyes wide open.” The Do’s and Don’ts of WhatsApp About Lines
Do keep it appropriate. Remember that your profile can be seen by various people in your life.
Don’t use offensive or controversial statements. It’s always wise to be respectful and considerate.
Do use emojis or symbols sparingly for added flair.
Don’t overdo it with complicated jargon or overly cryptic messages.
Expanding Your Attitude Expression Through Emojis and Symbols

Although words are powerful but become more saviour when blended with symbols and emojis since it’s more catching for human eyes to capture non-verbal language. For
example, a simple smiley reflects friendliness while a bicep symbol can reflect power and energy. That’s why these symbols must be used with the right words because matching words and symbols is very important. Here’s a selection of such emojis and symbols:
💪 Flexed Biceps: Strength and determination.
🔥 Fire: Passion and trendiness.
🦁 Lion: Courage and leadership.
🌟 Star: Excellence.
🏆 Trophy: Victory and success.
👑 Crown: Authority and power.
🚀 Rocket: Ambition and high goals.
🌪 Tornado: Impactful presence.
🥇 Medal: Top achievement.
⚡ Lightning Bolt: Energy and speed.
Rock Climber: Perseverance and adventure.
🤺 Fencer: Strategic thinking.
Weight Lifter: Physical strength.
🦅 Eagle: Freedom and high aspirations.
🌈 Rainbow: Hope and positivity.
🕶 Sunglasses: Coolness.
💼 Briefcase: Professional success.
🚧 Construction: Building something significant.
🐉 Dragon: Power and mystique.
🗡 Dagger: Bravery.
Leveraging Your About Line for Personal Branding

Personal branding has become an essential part of this era so the WhatsApp About line must be written clearly and wisely. It’s a great opportunity for you to show your true
personality to all people in your circle either from your office or family or friends. So it can complement your personal branding strategy whether you are a professional, an entrepreneur, or a student.
Conclusion
Your WhatsApp About lines can truly paint your personality on canvas if the right words are chosen. It’s a combination of your attitude, personality and expression and writing it in one or two lines is an art. By following our above-suggested rules, you can easily write an About line that not only reflects your attitude but also leaves a memorable impression on whoever reads your profile.
Keep it in mind, in today’s digital world your About line is not just a combination of words but it’s your attitude that is speaking. Choose it wisely!

A Comprehensive Guide: How to View Incognito History on Android
A common feature of web browsers is called “incognito mode,” which enables users to access the internet without leaving any digital trail of their activities on the device.
It can be a little challenging, though, if you need to view what someone else has been doing on their Android handset when it’s in private mode. This post will explain how to use a file manager app on an Android device to access incognito history.
How Does Incognito Mode Operate, and What Does It Mean?
Many web browsers on Android smartphones provide an option called “incognito mode” that lets users view websites without preserving their cookies, browsing history, or cache.
In essence, it splits off the user’s main browsing experience to establish a temporary one. The user’s browsing history, including websites visited, search terms entered, and form input, is not saved by the browser when it is in incognito mode.
Because it keeps others from viewing their browser history, this function might be very helpful for people who share a computer. It can also be useful for people who want to hide their internet activity from other people who might have access to their computer or other device.
All things considered, by keeping data about cookies, browsing history, and cache from being saved, incognito mode gives users a certain amount of privacy. Although it shouldn’t be relied upon for total anonymity, it can be a useful tool for individuals who want to keep their internet activity hidden.
Why See History on Android in Incognito Mode?
On an Android device, there are numerous reasons why someone might want to access their history in private mode. Say for instance:
Supervision of Parents:
It might be a good idea for parents to keep an eye on their kids’ internet activities to make sure they aren’t connecting with strangers or viewing offensive material. Even if their child is hiding their online behavior by utilizing incognito mode, parents can still gain more insight into their online activities by looking through their incognito history.
Employee Observation:
Employers may need to monitor how much time their staff members spend online on company-issued devices in order to make sure they aren’t wasting it or viewing private data.
Employers can see if workers are accessing sensitive data in incognito mode or visiting non-work-related websites during working hours by looking through the incognito history.
For Individual Use:
Occasionally, individuals may wish to examine their own private browser history in order to monitor their online behaviors or to get crucial data that they may have forgotten to bookmark.
Users don’t need to look through their normal browser history to locate websites they visited while using the incognito mode by accessing their incognito history.
How to View Incognito History on Android
Here are the ways to access incognito history on an Android device:
Step 1: Install a file manager app after downloading it.
You must download and install a file management app in order to see the incognito history file on an Android smartphone. The “ES File Explorer” software is a free and user-friendly file manager that is highly recommended among the various apps available on the Google Play Store.
Step 2: Locate the Chrome Browser Folder
Open the file management program after installing it, then select the “Android” folder located on the internal storage of your device. Open the “com.android.chrome” folder after that, followed by the “data” folder. This is the folder containing the data related to the Chrome browser.
Step 3: Access the User Data Folder
You may find the “User Data” folder inside the com.android.chrome subdirectory. To view the Chrome user data, open this folder.
Step 4: Find the History File for Incognito
Look for a file called “Default” inside the User Data folder. All of the user’s browsing history, including that from incognito tabs, is kept in this folder by the Chrome browser.
Access the “Default” folder first, and subsequently the “History” folder to see the user’s entire browsing history—including any time they spent using incognito mode.
What Other Ways to View Someone’s Incognito History on Android
Web browsers’ incognito mode is by default intended to keep cookies, browsing history, and other data hidden and not saved on your device. Nonetheless, there are a few methods available on Android to see someone’s incognito history:
- Accessing cache items: Even in incognito mode, your device may still be saving certain items, like movies, photos, and other data, in its temporary files or cache. Using a file management application, you can retrieve these files by going to the browser’s cache directory and looking through the files kept there.
- Examining your internet service provider’s (ISP) logs: Your ISP has the potential to record all of your online activities, including the history of your private browsing sessions. You can request your surfing history logs from your ISP, but this is not advised and might be against the law in some areas.
- Using third-party apps: On Android devices, third-party apps with the ability to see browsing history incognito are available in the Google Play Store. Individually designed innovations like uMobix or Flexispy, which can track your partner’s or spouse’s phone around-the-clock, are also available.
Remember that accessing your Android device’s incognito browsing history may not always work and that doing so defeats the point of incognito mode.
Tips for Maintaining Privacy on Android
Our recommendation is to use a virtual private network (VPN) to encrypt your internet traffic and conceal your IP address when utilizing incognito mode or browsing the internet in general. Other options include using privacy-focused browsers like DuckDuckGo or Tor, which don’t monitor your online activities.
Which Incognito Mode Browsers Offer the Highest Level of Security?
A degree of privacy and security is offered by the incognito or private browsing mode included in the majority of contemporary web browsers, including well-known ones like Chrome, Firefox, Safari, and Edge. However, not all browsers offer the same amount of protection and privacy while using incognito mode, so it may not always work.
Nevertheless, the following are a few of the most popular web browsers that offer a reasonably safe incognito mode for users:
- Brave: Brave is a privacy-focused web browser that features a “Private Window with Tor” private browsing mode that uses the Tor network to route your traffic, adding more security and anonymity layers.
- Firefox: If you use Firefox, you can browse privately without saving cookies, temporary files, or browsing history. Additionally, it disables scripts that use fingerprinting and third-party trackers to monitor your internet activities.
- High-level security and privacy are provided by the Tor Browser, which is built on Firefox and leverages the Tor network to encrypt and anonymize your internet traffic.
- DuckDuckGo Privacy Browser: This browser is designed with privacy in mind. It has a private browsing mode that encrypts your internet traffic, disables third-party trackers, and erases your browsing history when you close the program.
- Microsoft Edge: This browser has an InPrivate mode that keeps cookies, temporary files, and browsing history from being saved. Other kinds of web trackers and third-party trackers are also blocked by it.
Remember that your internet service provider and other organizations might still be able to monitor your online activities even when you are in incognito mode. For this reason, it’s crucial to take extra precautions to improve your security and privacy, like utilizing a virtual private network (VPN) and staying away from dubious or untrusted websites.
The Final Thought
We demonstrated how to use a file manager app on an Android device to see incognito history in this article. It’s crucial to respect people’s privacy and only use this tool with their consent, even though it might be helpful for keeping an eye on online behavior.
You may have a better and more secure surfing experience on your Android device by taking precautions to protect your privacy online.
Frequently Asked Questions
Is Google Able to View Private Search History?
Absolutely. Google may be able to observe what you do online, even while you are using incognito mode.
Is It Possible for My Parents to View My Wi-Fi Incognito History?
Indeed, your parents are able to view your WiFi incognito history. Also, the network administrator of your mobile network—your boss, the owner of the café, your parent, etc.—can view information about the websites you visit.
Is Your Internet Service Provider Able to View Your History in Incognito Mode?
Your history is visible to your ISP, yes. Internet service providers resemble your mobile network’s network administrators. Your internet activity is still visible to your ISP because using only affects data that is saved locally on your devices.
How Can I View Chrome’s Incognito History?
In the URL bar of your browser, type chrome://chrome/history/ to view the history of Chrome incognito mode. An alternative method for viewing your incognito history is to download Chrome addons.
Is My Phone’s Incognito History Visible to My Employer?
Your phone does not save your search history when you activate Incognito mode. However, the company’s IT department may monitor all network activity if you use the Wi-Fi or network at work, including any websites you visit while in Incognito mode. This means that your employer may be able to see the websites you visit even when using Incognito mode.